绕过的弯路
准备
------------frp的准备
------------SSR的安装
------------LNMP环境安装
------------BBR加速
FRP配置
------------frps服务器配置
------------frpc客户端配置
------------------------TCP类配置文件
------------------------http类网站配置文件
------------------------SSR穿透配置文件
Nginx配置
使用方法
-
为了将局域网服务开放到公网使用,使用frp实现内网穿透.
本文中使用的服务器位于境外,域名属境外,使用了cloudflare托管服务,需要穿透的网络在中国大陆.
实现目标:- 在公网通过带有https的域名访问位于内网的非https网站并实现其全部功能.
- 使公网设备以VPN或类似方式模拟内网环境,以直接访问位于内网的服务.
- 使得同在一个服务器上的frps/ssr/nginx三个服务完全兼容&端口共享.
大概结构: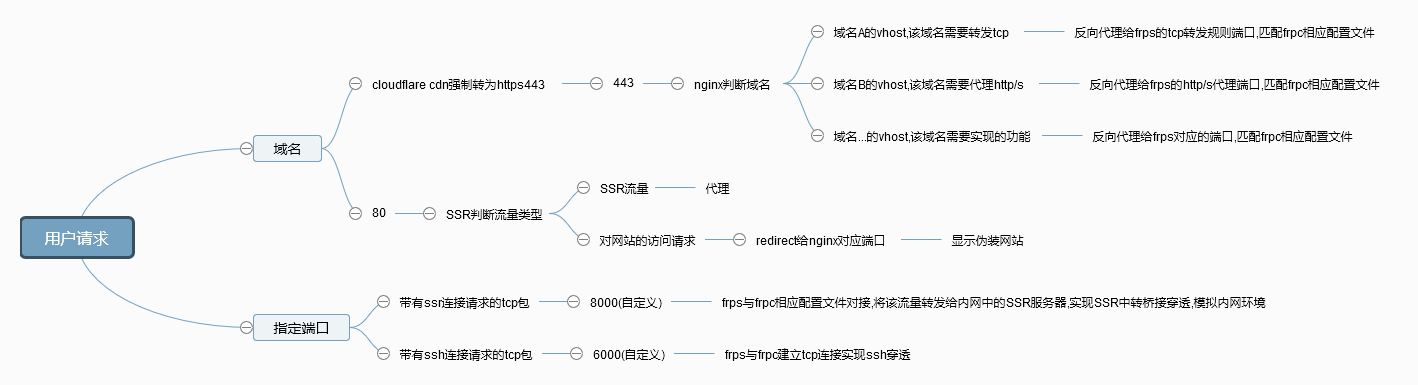
绕过的弯路
刚开始做的时候我使用的是大陆服务器和域名,延迟低速度快固然好,但是遇到了以下问题:
- 如果只使用ip访问将很不方便.
- 即使使用443也无法绕过备案机制了,还是会被发现并封停.
- 没有稳定长期的ssl证书.
- 若使用cloudflare会出现其cdn节点被墙导致无法访问网站的情况.
所以多次碰壁后我还是把主要服务放在境外.
准备
frp的准备
首先到frp的releases页面下载最新版的包到内网客户端(frpc)和公网服务器(frps)上,服务器和客户端架构未必相同,各自找各自对应的包.
https://github.com/fatedier/frp/releases
确认系统架构
arch在release中找到对应架构包后,在服务器和客户端都完成下载与解压
#下载包
wget --no-check-certificate https://github.com/fatedier/frp/releases/download/v0.29.0/frp_0.29.0_linux_amd64.tar.gz
#解压包
tar -xzvf frp_0.29.0_linux_amd64.tar.gz
#名字太长改成frp
mv frp_0.29.0_linux_amd64 frp
#确保 frps/c 程序具有可执行权限
cd frp
chmod +x frps #服务器
chmod +x frpc #客户端尝试运行frps,有返回帮助信息则成功,返回-bash: ./frps: cannot execute binary file: Exec format error表示下错版本了.
./frps --helpfrp中frpc是客户端使用的,frps是服务器使用的,至此都已准备好了frp程序.
SSR的安装
frps服务器上安装ssr是为了科学上网,而frpc上安装ssr是为了在公网模拟内网网路环境,类似vpn,需要哪个功能安装在哪个上.
在frpc客户端上安装ssr时设置的端口与后文的frpc客户端配置文件对应
在frps服务器上安装时需要伪装网站混淆,和后文的nginx配置部分相配合,注意设置端口80
vi /etc/shadowsocks.json
# 把 server_port 参数改成这样:
"server_port": 80,
# 把 redirect 参数改成这样:
"redirect": ["*:80#127.0.0.1:2399"],
#剩下的与nginx配置文件衔接,下文有举例LNMP环境安装
1.将域名ssl证书与密钥文件上传到服务器,稍后创建vhost用到
2.安装lnmp,只安装nginx
wget http://soft.vpser.net/lnmp/lnmp1.6.tar.gz -cO lnmp1.6.tar.gz && tar zxf lnmp1.6.tar.gz && cd lnmp1.6 && ./install.sh nginx安装完整lnmp
wget http://soft.vpser.net/lnmp/lnmp1.6.tar.gz -cO lnmp1.6.tar.gz && tar zxf lnmp1.6.tar.gz && cd lnmp1.6 && ./install.sh lnmp3.编辑默认nginx配置文件
vi /usr/local/nginx/conf/nginx.conf因nginx默认监听占用80会与ssr监听80冲突所以
注释或删掉server{}段内容,注意不要删除文件结尾的include vhost/*.conf;,如下:
user www www;
worker_processes auto;
worker_cpu_affinity auto;
error_log /home/wwwlogs/nginx_error.log crit;
pid /usr/local/nginx/logs/nginx.pid;
#Specifies the value for maximum file descriptors that can be opened by this process.
worker_rlimit_nofile 51200;
events
{
use epoll;
worker_connections 51200;
multi_accept off;
accept_mutex off;
}
http
{
include mime.types;
default_type application/octet-stream;
server_names_hash_bucket_size 128;
client_header_buffer_size 32k;
large_client_header_buffers 4 32k;
client_max_body_size 50m;
sendfile on;
sendfile_max_chunk 512k;
tcp_nopush on;
keepalive_timeout 60;
tcp_nodelay on;
fastcgi_connect_timeout 300;
fastcgi_send_timeout 300;
fastcgi_read_timeout 300;
fastcgi_buffer_size 64k;
fastcgi_buffers 4 64k;
fastcgi_busy_buffers_size 128k;
fastcgi_temp_file_write_size 256k;
gzip on;
gzip_min_length 1k;
gzip_buffers 4 16k;
gzip_http_version 1.1;
gzip_comp_level 2;
gzip_types text/plain application/javascript application/x-javascript text/javascript text/css application/xml application/xml+rss;
gzip_vary on;
gzip_proxied expired no-cache no-store private auth;
gzip_disable "MSIE [1-6]\.";
#limit_conn_zone $binary_remote_addr zone=perip:10m;
##If enable limit_conn_zone,add "limit_conn perip 10;" to server section.
server_tokens off;
access_log off;
#server
# {
# listen 80 default_server reuseport;
# #listen [::]:80 default_server ipv6only=on;
# server_name _;
# index index.html index.htm index.php;
# root /home/wwwroot/default;
#
# #error_page 404 /404.html;
#
# # Deny access to PHP files in specific directory
# #location ~ /(wp-content|uploads|wp-includes|images)/.*\.php$ { deny all; }
#
# include enable-php.conf;
#
# location /nginx_status
# {
# stub_status on;
# access_log off;
# }
#
# location ~ .*\.(gif|jpg|jpeg|png|bmp|swf)$
# {
# expires 30d;
# }
#
# location ~ .*\.(js|css)?$
# {
# expires 12h;
# }
#
# location ~ /.well-known {
# allow all;
# }
#
# location ~ /\.
# {
# deny all;
# }
#
# access_log /home/wwwlogs/access.log;
# }
include vhost/*.conf;
}4.将各个域名&二级域名指向ip,ssr的伪装域名不要加cdn和https
BBR加速
本优化项在所有功能都正常运行后再尝试添加,若导致frp失效则关闭.
16.04
wget -N --no-check-certificate "https://raw.githubusercontent.com/chiakge/Linux-NetSpeed/master/tcp.sh" && chmod +x tcp.sh && ./tcp.sh18.04
wget -N --no-check-certificate "https://raw.githubusercontent.com/chiakge/Linux-NetSpeed/master/tcp.sh"
apt install make gcc -y
sed -i 's#/usr/bin/gcc-4.9#/usr/bin/gcc#g' '/root/tcp.sh'
chmod +x tcp.sh && ./tcp.shFRP配置
本文涉及三个frpc配置文件&一个frps文件.
本文只涉及部分frp的简单配置,完整功能与配置参阅
FRP中文文档
[FRPS完整配置文件]3
# [common] is integral section
[common]
# A literal address or host name for IPv6 must be enclosed
# in square brackets, as in "[::1]:80", "[ipv6-host]:http" or "[ipv6-host%zone]:80"
bind_addr = 0.0.0.0
bind_port = 7000
# udp port to help make udp hole to penetrate nat
bind_udp_port = 7001
# udp port used for kcp protocol, it can be same with 'bind_port'
# if not set, kcp is disabled in frps
kcp_bind_port = 7000
# specify which address proxy will listen for, default value is same with bind_addr
# proxy_bind_addr = 127.0.0.1
# if you want to support virtual host, you must set the http port for listening (optional)
# Note: http port and https port can be same with bind_port
vhost_http_port = 80
vhost_https_port = 443
# response header timeout(seconds) for vhost http server, default is 60s
# vhost_http_timeout = 60
# set dashboard_addr and dashboard_port to view dashboard of frps
# dashboard_addr's default value is same with bind_addr
# dashboard is available only if dashboard_port is set
dashboard_addr = 0.0.0.0
dashboard_port = 7500
# dashboard user and passwd for basic auth protect, if not set, both default value is admin
dashboard_user = admin
dashboard_pwd = admin
# dashboard assets directory(only for debug mode)
# assets_dir = ./static
# console or real logFile path like ./frps.log
log_file = ./frps.log
# trace, debug, info, warn, error
log_level = info
log_max_days = 3
# disable log colors when log_file is console, default is false
disable_log_color = false
# auth token
token = 12345678
# heartbeat configure, it's not recommended to modify the default value
# the default value of heartbeat_timeout is 90
# heartbeat_timeout = 90
# only allow frpc to bind ports you list, if you set nothing, there won't be any limit
allow_ports = 2000-3000,3001,3003,4000-50000
# pool_count in each proxy will change to max_pool_count if they exceed the maximum value
max_pool_count = 5
# max ports can be used for each client, default value is 0 means no limit
max_ports_per_client = 0
# if subdomain_host is not empty, you can set subdomain when type is http or https in frpc's configure file
# when subdomain is test, the host used by routing is test.frps.com
subdomain_host = frps.com
# if tcp stream multiplexing is used, default is true
tcp_mux = true
# custom 404 page for HTTP requests
# custom_404_page = /path/to/404.html[FRPC完整配置文件]4
# [common] is integral section
[common]
# A literal address or host name for IPv6 must be enclosed
# in square brackets, as in "[::1]:80", "[ipv6-host]:http" or "[ipv6-host%zone]:80"
server_addr = 0.0.0.0
server_port = 7000
# if you want to connect frps by http proxy or socks5 proxy, you can set http_proxy here or in global environment variables
# it only works when protocol is tcp
# http_proxy = http://user:[email protected]:8080
# http_proxy = socks5://user:[email protected]:1080
# console or real logFile path like ./frpc.log
log_file = ./frpc.log
# trace, debug, info, warn, error
log_level = info
log_max_days = 3
# disable log colors when log_file is console, default is false
disable_log_color = false
# for authentication
token = 12345678
# set admin address for control frpc's action by http api such as reload
admin_addr = 127.0.0.1
admin_port = 7400
admin_user = admin
admin_pwd = admin
# Admin assets directory. By default, these assets are bundled with frpc.
# assets_dir = ./static
# connections will be established in advance, default value is zero
pool_count = 5
# if tcp stream multiplexing is used, default is true, it must be same with frps
tcp_mux = true
# your proxy name will be changed to {user}.{proxy}
user = your_name
# decide if exit program when first login failed, otherwise continuous relogin to frps
# default is true
login_fail_exit = true
# communication protocol used to connect to server
# now it supports tcp and kcp and websocket, default is tcp
protocol = tcp
# if tls_enable is true, frpc will connect frps by tls
tls_enable = true
# specify a dns server, so frpc will use this instead of default one
# dns_server = 8.8.8.8
# proxy names you want to start seperated by ','
# default is empty, means all proxies
# start = ssh,dns
# heartbeat configure, it's not recommended to modify the default value
# the default value of heartbeat_interval is 10 and heartbeat_timeout is 90
# heartbeat_interval = 30
# heartbeat_timeout = 90
# 'ssh' is the unique proxy name
# if user in [common] section is not empty, it will be changed to {user}.{proxy} such as 'your_name.ssh'
[ssh]
# tcp | udp | http | https | stcp | xtcp, default is tcp
type = tcp
local_ip = 127.0.0.1
local_port = 22
# true or false, if true, messages between frps and frpc will be encrypted, default is false
use_encryption = false
# if true, message will be compressed
use_compression = false
# remote port listen by frps
remote_port = 6001
# frps will load balancing connections for proxies in same group
group = test_group
# group should have same group key
group_key = 123456
# enable health check for the backend service, it support 'tcp' and 'http' now
# frpc will connect local service's port to detect it's healthy status
health_check_type = tcp
# health check connection timeout
health_check_timeout_s = 3
# if continuous failed in 3 times, the proxy will be removed from frps
health_check_max_failed = 3
# every 10 seconds will do a health check
health_check_interval_s = 10
[ssh_random]
type = tcp
local_ip = 127.0.0.1
local_port = 22
# if remote_port is 0, frps will assign a random port for you
remote_port = 0
# if you want to expose multiple ports, add 'range:' prefix to the section name
# frpc will generate multiple proxies such as 'tcp_port_6010', 'tcp_port_6011' and so on.
[range:tcp_port]
type = tcp
local_ip = 127.0.0.1
local_port = 6010-6020,6022,6024-6028
remote_port = 6010-6020,6022,6024-6028
use_encryption = false
use_compression = false
[dns]
type = udp
local_ip = 114.114.114.114
local_port = 53
remote_port = 6002
use_encryption = false
use_compression = false
[range:udp_port]
type = udp
local_ip = 127.0.0.1
local_port = 6010-6020
remote_port = 6010-6020
use_encryption = false
use_compression = false
# Resolve your domain names to [server_addr] so you can use http://web01.yourdomain.com to browse web01 and http://web02.yourdomain.com to browse web02
[web01]
type = http
local_ip = 127.0.0.1
local_port = 80
use_encryption = false
use_compression = true
# http username and password are safety certification for http protocol
# if not set, you can access this custom_domains without certification
http_user = admin
http_pwd = admin
# if domain for frps is frps.com, then you can access [web01] proxy by URL http://test.frps.com
subdomain = web01
custom_domains = web02.yourdomain.com
# locations is only available for http type
locations = /,/pic
host_header_rewrite = example.com
# params with prefix "header_" will be used to update http request headers
header_X-From-Where = frp
health_check_type = http
# frpc will send a GET http request '/status' to local http service
# http service is alive when it return 2xx http response code
health_check_url = /status
health_check_interval_s = 10
health_check_max_failed = 3
health_check_timeout_s = 3
[web02]
type = https
local_ip = 127.0.0.1
local_port = 8000
use_encryption = false
use_compression = false
subdomain = web01
custom_domains = web02.yourdomain.com
# if not empty, frpc will use proxy protocol to transfer connection info to your local service
# v1 or v2 or empty
proxy_protocol_version = v2
[plugin_unix_domain_socket]
type = tcp
remote_port = 6003
# if plugin is defined, local_ip and local_port is useless
# plugin will handle connections got from frps
plugin = unix_domain_socket
# params with prefix "plugin_" that plugin needed
plugin_unix_path = /var/run/docker.sock
[plugin_http_proxy]
type = tcp
remote_port = 6004
plugin = http_proxy
plugin_http_user = abc
plugin_http_passwd = abc
[plugin_socks5]
type = tcp
remote_port = 6005
plugin = socks5
plugin_user = abc
plugin_passwd = abc
[plugin_static_file]
type = tcp
remote_port = 6006
plugin = static_file
plugin_local_path = /var/www/blog
plugin_strip_prefix = static
plugin_http_user = abc
plugin_http_passwd = abc
[plugin_https2http]
type = https
custom_domains = test.yourdomain.com
plugin = https2http
plugin_local_addr = 127.0.0.1:80
plugin_crt_path = ./server.crt
plugin_key_path = ./server.key
plugin_host_header_rewrite = 127.0.0.1
plugin_header_X-From-Where = frp
[secret_tcp]
# If the type is secret tcp, remote_port is useless
# Who want to connect local port should deploy another frpc with stcp proxy and role is visitor
type = stcp
# sk used for authentication for visitors
sk = abcdefg
local_ip = 127.0.0.1
local_port = 22
use_encryption = false
use_compression = false
# user of frpc should be same in both stcp server and stcp visitor
[secret_tcp_visitor]
# frpc role visitor -> frps -> frpc role server
role = visitor
type = stcp
# the server name you want to visitor
server_name = secret_tcp
sk = abcdefg
# connect this address to visitor stcp server
bind_addr = 127.0.0.1
bind_port = 9000
use_encryption = false
use_compression = false
[p2p_tcp]
type = xtcp
sk = abcdefg
local_ip = 127.0.0.1
local_port = 22
use_encryption = false
use_compression = false
[p2p_tcp_visitor]
role = visitor
type = xtcp
server_name = p2p_tcp
sk = abcdefg
bind_addr = 127.0.0.1
bind_port = 9001
use_encryption = false
use_compression = falsefrps服务器配置
我的配置文件:
[common]
bind_port = 21
#frps服务端口,考虑到服务器在境外,也许21口会降低一些被墙风险,心理作用,后面的客户端需要此端口
token = 80808080
#frps服务端密码,后面的客户端需要此密钥
authentication_timeout = 900
#认证超时时间,由于时间戳会被用于加密认证,防止报文劫持后被他人利用
#因此服务端与客户端所在机器的时间差不能超过这个时间(秒)
#默认为900秒,即15分钟,如果设置成0就不会对报文时间戳进行超时验证
vhost_http_port = 21
#专门用于穿透内网中http网站,端口与服务端口相同并不会导致冲突,原因见下文
#vhost_https_port = 10443 穿透https网站,本文中用不到
#subdomain_host = example.com
#此设置需要配合客户端设置,仅在穿透到内网中的 http 或 https 时有用(可选)
#假设此项设置为 example.com,客户端配置 http 时将 subdomain 设置为 test,
#则你将 test.example.com 解析到服务端后,可以使用此域名来访问客户端对应的 http
[ruige]
#该项与下文配置文件对应,名字必须对应,除基本的common外,还需要一个特殊的配置类别,原因见下文
listen_port = 6001
# 监听6001端口.这个单独的配置独占6001端口,与common的配置区别开frp有端口复用功能,可以自动识别.
目前 frps 中的 vhost_http_port 和 vhost_https_port 支持配置成和 bind_port 为同一个端口,frps 会对连接的协议进行分析,之后进行不同的处理。
例如在某些限制较严格的网络环境中,可以将 bind_port 和 vhost_https_port 都设置为 443。
单独列出[ruige]服务项(ruige是内网网站)而不单纯使用vhost_http_port是因为在测试中发现单纯的http穿透无法使得该网站所有功能正常运行,如该网站涉及到用户上传代码,服务器验证后返回给用户结果与报错信息,这个功能在http穿透中无法实现,所以转而对所有网站请求数据都使用tcp封包再进行传输,这样网站功能可以完整运行,详见下面的客户端配置文件.
frpc客户端配置
客户端的配置文件书写是决定功能的关键,上文的完整配置文件依然没有涵盖一些特殊操作
本文涉及的3项功能中有两项都是官方没举例过的,frp的可拓展性是很强的.
注意:在一台frpc客户端上可以书写多个.ini配置文件并分别运行,注意端口冲突和自定义项目名不要冲突即可分开编辑可以将功能模块化,便于排错,减少冲突
TCP类配置文件
[common]
#必写部分,配置文件开始
server_addr = 157.245.xxx.xxx
#frps服务器ip
server_port = 21
#frps服务器端口,即填写服务端配置中的 bind_port
token = 80808080
#frps服务器密码
tls_enable = true
#从 v0.25.0 版本开始 frpc 和 frps 之间支持通过 TLS 协议加密传输。通过在 frpc.ini 的 common 中配置 tls_enable = true 来启用此功能,安全性更高。为了端口复用,frp 建立 TLS 连接的第一个字节为 0x17。注意: 启用此功能后除 xtcp 外,不需要再设置 use_encryption
[ruige]
#自定义一个配置名称,格式为“[名称]”
#ruige功能部分,这个网站即上文提及的需要将所有http请求封包成tcp的网站,单纯的tcp传输无法通过域名访问,所以拼凑成了如下配置,如果遇到类似http模式不能实现全部功能的网站,同样可以考虑使用类似办法
type = tcp
#该网站类型一定要是tcp
#其他类似的还有udp,xtcp等详见中文文档说明
local_ip = 222.27.166.246
#需要被穿透的内网网站ip
local_port = 80
#该网站端口
remote_port = 6001
#与上文frps的[ruige]模块中的listen_port对应
custom_domains = rg.nefu.cc
#自定义域名,这个不同于 subdomain,你可以设置与 subdomain_host 无关的其他域名,subdomain_host更适合二级域名
#subdomain 与 custom_domains 中至少有一个必须要设置,个人喜欢直接使用custom_domains
#如果需要直接通过ip访问则此处填frps服务器ip
#use_encryption = false
#已经使用tls传输就没有必要使用加密参数了
#use_compression = false
#是否压缩客户端与服务端之间的通信,默认是 false
#压缩可以节省流量,但需要消耗 CPU 资源
#加密自然也会消耗 CPU 资源,但是不大
#host_header_rewrite = rg.nefu.cc
#重写 host header,相当于反向代理中的“发送域名”
#如果设置了,转发 http 时,请求中的 host 会被替换成这个
#一般情况下不需要用到这个,可以不写这项
[ssh]
type = tcp
local_ip = 127.0.0.1
local_port = 22
#需要穿透的ssh端口
remote_port = 6000
#frp 服务端的远程监听端口,即你访问服务端的 remote_port 就相当于访问
#客户端的 local_port,如果填0则会随机分配一个端口
#local_port = 6010-6020,6022,6024-6028
#remote_port = 16010-16020,16022,16024-16028
#本地端口和远程端口可以指定多个范围,如上格式,且范围之间必须一一对应http类网站配置文件
[common]
server_addr = 157.245.xxx.xxx
server_port = 21
token = 80808080
tls_enable = true
[dawuxuanke]
# 自定义一个配置名称,格式为“[名称]”
type = http
#连接类型,填 http 或 https
local_ip = 222.27.175.13
local_port = 80
#需要穿透的网站ip及其访问端口
custom_domains = dw.nefu.cc
#如果需要直接通过ip访问则此处填frps服务器ip
#自定义域名,这个不同于 subdomain,你可以设置与 subdomain_host 无关的其他域名
#subdomain 与 custom_domains 中至少有一个必须要设置
#http_user = admin
#http_pwd = admin
#自定义访问网站的用户名和密码,如果不定义的话谁都可以访问,会不安全
#有些路由器如果从内部访问web是不需要用户名密码的,因此需要在这里加一层密码保护
#如果你发现不加这个密码保护,路由器配置页面原本的用户认证能正常生效的话,可以不加
#subdomain = web01
#还记得我们在服务端配置的 subdomain_host = example.com 吗
#假设这里我们填 web01,那么你将 web01.example.com 解析到服务端ip后
#你就可以使用 域名:端口 来访问你的 http 了
#这个域名的作用是用来区分不同的 http,因为你可以配置多个这样的配置
#host_header_rewrite = dev.yourdomain.com
#重写 host header,相当于反向代理中的“发送域名”
#如果设置了,转发 http 时,请求中的 host 会被替换成这个
#一般情况下不需要用到这个,可以不写这项
#locations = /abc,/def
#匹配路径,可以设置多个,用逗号分隔,比如你设置 locations 为以下这个,
#那么所有 http://xxx/abc 和 http://xxx/def 都会被转发到 http://xxx/
#如果不需要这个功能可以不写这项,就直接该怎么访问就怎么访问SSR穿透配置文件
转发ssr请求其实属于tcp类,但是需要和frpc客户端上的ssr相衔接所以单独记录.
先在frpc客户端上安装ssr服务器
wget --no-check-certificate https://raw.githubusercontent.com/teddysun/shadowsocks_install/master/shadowsocksR.sh
chmod +x shadowsocksR.sh
./shadowsocksR.sh 2>&1 | tee shadowsocksR.log配置上none+plain+origin应该就可以.我使用了none+plain+auth_chain_a
假设端口设为了8899
frpc配置文件:
[common]
server_addr = 157.245.xxx.xxx
server_port = 21
token = 80808080
[ssr]
type = tcp
local_ip = 127.0.0.1
#内网ssr服务器ip,因frpc上同时装了ssr所以是local_host
local_port = 8899
#内网ssr服务器的端口,对应刚才安装的ssr的端口
remote_port = 6002
#连接frps公网服务器时的端口这样的配置下,在手机电脑等ssr客户端上的配置就应该是:
- 服务器:frps公网ip
- 远程端口:6002
- 密码:内网ssr设置的密码
- 加密方法:none
- 协议:auth_chain_a
- 混淆:plain
- 路由:全局
这样就实现了ssr的桥接穿透,ssr客户端设备直接访问内网ip即可访问网站.
Nginx配置
本文涉及三个nginx配置文件.
新建vhost
lnmp vhost addssl部分使用自定义证书密钥,前文已经准备好,完成后网站目录里不用放东西,直接去编辑该网站nginx配置文件
updatedb
locate 域名.conf
vi /路径/域名.conf主要工作是为配置文件添加反向代理,对用户请求的不同域名做出不同转发动作.
反代需要加入如下模块
location / {
proxy_pass http://xxx.xx;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}我的配置文件:
rg.nefu.cc.conf([ruige])
server
{
listen 443 ssl http2;
#listen [::]:443 ssl http2;
server_name rg.nefu.cc ;
# index index.html index.htm index.php default.html default.htm default.php;
#root /home/wwwroot/rg.nefu.cc;
ssl_certificate /root/nefu.cc.pem;
ssl_certificate_key /root/nefu.cc.key;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers "TLS13-AES-256-GCM-SHA384:TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-128-GCM-SHA256:TLS13-AES-128-CCM-8-SHA256:TLS13-AES-128-CCM-SHA256:EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5";
ssl_session_cache builtin:1000 shared:SSL:10m;
# openssl dhparam -out /usr/local/nginx/conf/ssl/dhparam.pem 2048
ssl_dhparam /usr/local/nginx/conf/ssl/dhparam.pem;
# include rewrite/none.conf;
#error_page 404 /404.html;
# Deny access to PHP files in specific directory
#location ~ /(wp-content|uploads|wp-includes|images)/.*\.php$ { deny all; }
# include enable-php.conf;
location / {
proxy_pass http://127.0.0.1:6001;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}收到对rg.nefu.cc的访问请求后代理到本地的6001端口也就是frp的[ruige]配置.
dw.nefu.cc.conf([dawuxuanke])
server
{
listen 443 ssl http2;
#listen [::]:443 ssl http2;
server_name dw.nefu.cc ;
# index index.html index.htm index.php default.html default.htm default.php;
#root /home/wwwroot/rg.nefu.cc;
ssl_certificate /root/nefu.cc.pem;
ssl_certificate_key /root/nefu.cc.key;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers "TLS13-AES-256-GCM-SHA384:TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-128-GCM-SHA256:TLS13-AES-128-CCM-8-SHA256:TLS13-AES-128-CCM-SHA256:EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5";
ssl_session_cache builtin:1000 shared:SSL:10m;
# openssl dhparam -out /usr/local/nginx/conf/ssl/dhparam.pem 2048
ssl_dhparam /usr/local/nginx/conf/ssl/dhparam.pem;
# include rewrite/none.conf;
#error_page 404 /404.html;
# Deny access to PHP files in specific directory
#location ~ /(wp-content|uploads|wp-includes|images)/.*\.php$ { deny all; }
# include enable-php.conf;
location / {
proxy_pass http://127.0.0.1:21;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}转发对dw.nefu.cc的请求到本地21口进而被frp的http模块发送给内网[dawuxuanke]客户端.
ssr伪装网站
在网站目录下随便放个网站模板,配置文件设置一个其他端口如2399,该端口将由ssr转发至.
server
{
listen 127.0.0.1:2399;
#listen [::]:80;
server_name sp.j000e.co ;
index index.html index.htm index.php default.html default.htm default.php;
root /home/wwwroot/sp.j000e.co;
include rewrite/none.conf;
#error_page 404 /404.html;
# Deny access to PHP files in specific directory
#location ~ /(wp-content|uploads|wp-includes|images)/.*\.php$ { deny all; }
include enable-php.conf;
location ~ .*\.(gif|jpg|jpeg|png|bmp|swf)$
{
expires 30d;
}
location ~ .*\.(js|css)?$
{
expires 12h;
}
location ~ /.well-known {
allow all;
}
location ~ /\.
{
deny all;
}
access_log off;
}使用方法
frp的启动与关闭
在终端中启动frps/c(关闭终端会停止程序,实时日志显示方便调试时使用):
cd frp
./frps -c ./frps.ini
./frpc -c ./frpc.ini
#-c 后跟不同配置文件在后台运行frps/c:
nohup ./frps -c ./frps.ini &
nohup ./frpc -c ./frpc.ini &关闭frp进程:
pkill frps
pkill frpcnginx的操作
每次修改配置文件后都要重启nginx
lnmp nginx restartssr操作
启动:/etc/init.d/shadowsocks start
停止:/etc/init.d/shadowsocks stop
重启:/etc/init.d/shadowsocks restart
状态:/etc/init.d/shadowsocks status
配置文件路径:/etc/shadowsocks.json
日志文件路径:/var/log/shadowsocks.log
代码安装目录:/usr/local/shadowsocks
-
版权声明:本文为原创文章,版权归Joe所有,转载请注明出处.
本文链接:https://www.j000e.com/linuxserver/frpserver.html

本作品采用知识共享署名-非商业性使用 4.0 国际许可协议进行许可。